Cybersecurity Awareness Month: MFA ist wichtiger denn je
Der Oktober ist der Cybersecurity Awareness Month (CAM), eine globale Initiative zur Sensibilisierung für Online-Sicherheit. CAM ist eine jährliche Erinnerung daran, dass Cybersecurity auf vier grundlegenden Praktiken basiert, die jedes Unternehmen zu seinem Schutz befolgen muss.

CAM Core 4 – vier einfache Schritte, um online sicher zu bleiben, über CISA
Von diesen Kernpraktiken ist die Aktivierung der Multi-Faktor-Authentifizierung (MFA) eine der effektivsten Methoden zum Schutz Ihrer Konten und Daten. Der National Cybersecurity Alliance zufolge können durch Aktivierung der MFA 99 % der automatisierten Hacking-Angriffe verhindert werden. MFA ist jedoch nicht unfehlbar, daher sollten wir uns genauer ansehen, was sie ist, wie sie funktioniert und wie sie optimal genutzt werden kann.
Was ist MFA und wie ist es entstanden?
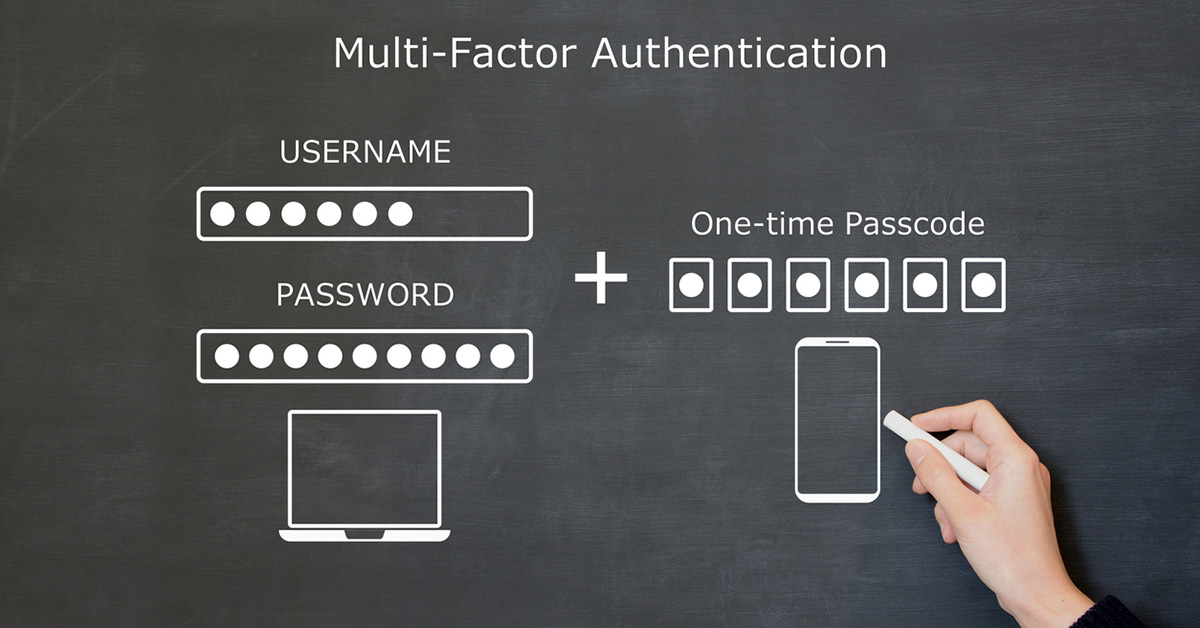
MFA ist ein Security-Prozess, der von Nutzern verlangt, ihre Identität mit zwei oder mehr unabhängigen Faktoren zu verifizieren. Diese Faktoren fallen in mehrere Kategorien:
- Wissen: Etwas, das nur Sie wissen (Passwort, PIN, Sicherheitsfrage)
- Besitz: Etwas, das Sie besitzen (Smartphone, Hardware-Token, Smartcard, Einmal-Passwort)
- Inhärenz: Etwas, das Sie sind (Fingerabdruck, Gesichtserkennung, Stimmerkennung)
- Standort und Verhalten: Wo Sie sich befinden (Standort, IP-Adresse, Geofencing; verwendet in adaptiver MFA)
Der genaue Ursprung von MFA ist nicht bekannt, aber das Konzept gibt es schon seit Jahrzehnten. Geldautomaten werden häufig als die erste gängige Verwendung von MFA genannt, da sie den Besitz eines physischen Schecks oder einer Karte und die Kenntnis der PIN erforderten. Sie mussten beides besitzen, um Zugriff auf das zugehörige Konto zu erhalten.
Diese Sicherheitsmaßnahme wurde erst viel später als MFA bekannt, als Regulierungs- und Normungsbehörden begannen, sie als Kontrollmaßnahme einzusetzen. Mit der Zunahme von Online-Diensten und Cyber-Bedrohungen nahm die Nutzung von MFA als Cybersecurity-Tool zu und wurde auf mobile Apps, Biometrie und die adaptiven risikobasierten (kontextbezogenen) Prüfungen ausgeweitet, die in Zero-Trust-Umgebungen verwendet werden.
MFA und Zwei-Faktor-Authentifizierung (2FA) werden manchmal synonym verwendet, sind jedoch zwei unterschiedliche Verfahren. 2FA erfordert genau zwei Faktoren aus verschiedenen Kategorien, was viele Verbraucheranwendungen nutzen, um Kundenanmeldungen zu sichern. MFA kann zwei oder mehr Arten von Zugangsdaten kombinieren, wie ein Passwort, ein mobiles Gerät oder eine biometrische Überprüfung. Der Einsatz von mehr als zwei Faktoren oder kontextbezogenen Prüfungen ist deutlich sicherer als 2FA.
Wie Angreifer 2FA/MFA umgehen
Angreifer sind besser darin geworden, die MFA-Security zu umgehen. Hier sind einige der Methoden, mit denen sie die zweite Authentifizierung umgehen:
- Phishing-Kits wie Whisper 2FA, die Einmalcodes abfangen können.
- Adversary-in-the-Middle (AiTM) oder Proxy-Angriffe, die Zugangsdaten und MFA-Codes in Echtzeit an Angreifer weiterleiten können. Diese Angriffe fangen den Datenverkehr ab und manipulieren die Authentifizierung.
- MFA-Ermüdung/Push-Bombing ist ein Angriff, der Nutzer mit wiederholten Login-/MFA-Aufforderungen überflutet. Diese Taktik funktioniert, wenn Benutzer die Anmeldung bestätigen, nur damit die Warnungen aufhören.
- SIM-Swap-Angriffe beinhalten, dass Cyberkriminelle Telefonnummern kapern, um Autorisierungscodes abzufangen. Hier ist ein Beispiel für einen SIM-Swap bei der US Security and Exchange Commission.
- Helpdesk-/Social-Engineering-Betrug, bei dem sich Cyberkriminelle als Nutzer ausgeben und IT-Mitarbeiter dazu bringen, Zugriff auf ein Konto zu gewähren.
Sie können sich gegen diese Angriffe mit Phishing-resistenter MFA (Hardware-Schlüssel, App-basierte Authentifikationen) verteidigen, Nutzer über Push-Ermüdung und Phishing aufklären und Helpdesk- und Kontowiederherstellungsverfahren verstärken.
Bereitstellung und Verwaltung von MFA
Eine erfolgreiche MFA-Einführung beginnt mit einer Strategie und Nutzerschulungen. Informieren Sie Nutzer über Zugangsdatenangriffe und warum MFA eine so wichtige Schutzmaßnahme ist. Wie bei jedem IT-Projekt wird die Unterstützung durch die Beteiligten die Einführung wesentlich reibungsloser gestalten. Die Zusammenarbeit mit den Beteiligten wird Ihnen auch dabei helfen, die Risikostufen und MFA-Anforderungen für Nutzer und Gruppen zu bestimmen.
Wenn Sie bereit sind, die Bereitstellung zu starten, beginnen Sie mit den privilegierten Konten. Schützen Sie die Administrator- und Führungskräftekonten, bevor Sie den Schutz auf die übrigen Nutzer ausweiten. Stellen Sie sicher, dass Sie alles abdecken – VPNs, E-Mail, Fernzugriff, SaaS- und Cloud-Anwendungen usw. Verwenden Sie gegebenenfalls eine stärkere Authentifizierung für Konten mit höherem Risiko.
Wenn möglich, setzen Sie Single Sign-On (SSO), adaptive MFA und Push-basierte Authentifizierung ein, um den Nutzern die sichere Authentifizierung zu erleichtern. Und vergessen Sie nicht, eine sichere Wiederherstellungsrichtlinie und Backup-Optionen festzulegen, Nutzer immer wieder zu schulen und das Offboarding von ausscheidenden Mitarbeitern durchzuführen.
Über MFA hinaus: Zero Trust Access
Während MFA eine kritische Verteidigungsebene darstellt, geht der Zero-Trust-Zugriff noch weiter. Zero Trust geht davon aus, dass keinem Nutzer oder Gerät grundsätzlich vertraut wird, auch nicht innerhalb des Netzwerks. Moderne Zero-Trust-Plattformen wie Barracuda SecureEdge Zero Trust Access kombinieren MFA mit erweiterten Zugriffskontrollen, um unbefugten Zugriff zu blockieren – selbst wenn Angreifer über gültige Zugangsdaten oder Sitzungstoken verfügen.
Cybersecurity ist eine gemeinsame Verantwortung. Die Aktivierung von MFA ist einer der einfachsten und effektivsten Schritte, die Sie ergreifen können, um sich und Ihr Unternehmen zu schützen. Da Phishing-Kits und Adversary-in-the-Middle-Angriffe immer ausgefeilter werden, ist eine starke, Phishing-resistente MFA unerlässlich. Ziehen Sie außerdem die Umstellung auf Zero-Trust-Zugriff für noch besseren Schutz in Betracht.

Bericht über E-Mail-Sicherheitsverletzungen 2025
Wichtige Erkenntnisse über die Erfahrungen mit und Auswirkungen von E-Mail-Sicherheitsverletzungen auf Unternehmen weltweit
Abonnieren Sie den Barracuda-Blog.
Melden Sie sich an, um aktuelle Bedrohungsinformationen, Branchenkommentare und mehr zu erhalten.

Der MSP Customer Insight Report 2025
Ein globaler Blick darauf, was Organisationen von ihren Cybersecurity Managed Service Providers benötigen und erwarten.





